“People, if you didn’t get the memo, we’re all going to the cloud” – Steve Van Till, President & CEO, Brivo
First, a little background… A quick history on the cloud and how it came to be so widely adopted and important for business.
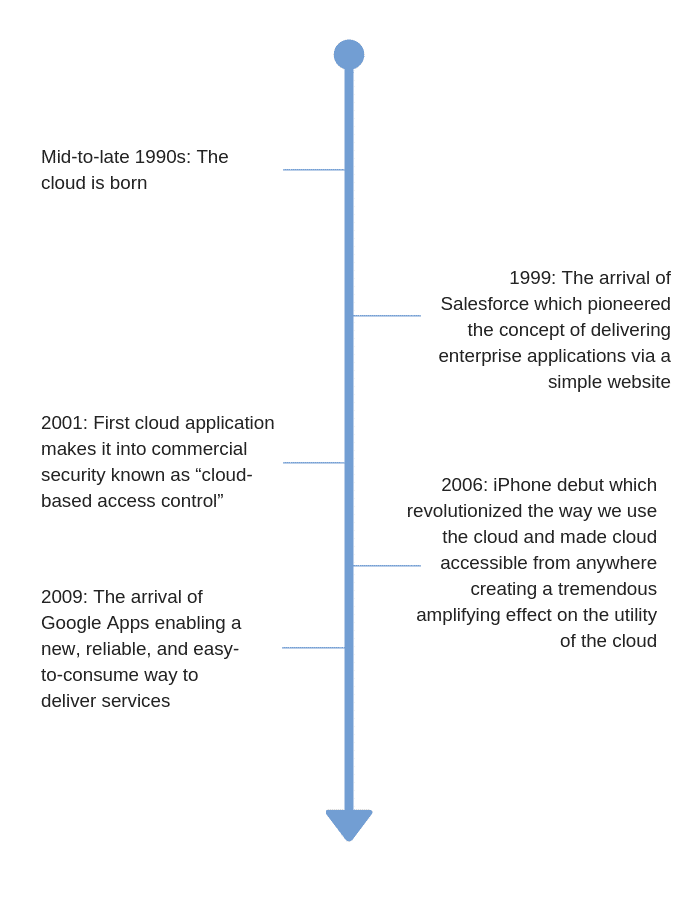
Cloud technology continues to become more ingrained in both our personal and professional lives due to its convenience, ease of use, flexibility and scalability. The cloud is here to stay.
Why should physical security professionals move to the cloud?
Every new technology born after the inception of the cloud uses the cloud or leverages it in some capacity. The cloud is a convenient and powerful platform which is why we see a thriving SaaS market and the massive expansion of IoT products. You are likely familiar with these products already, but what is the cloud’s role in physical security? Many industries are now entirely built on the cloud including: finance, enterprise resource planning, e-commerce and logistics. In fact, new residential security is 100% cloud-based. Today, most security vendors leverage the cloud. The physical security industry has been slow to adopt cloud, but it is where new opportunity lies. It offers businesses increased security and unlimited scalability. Ultimately, the cloud offers control of both building security and employee whereabouts. Cloud technology has and will change the way we conduct business.
What’s the Opportunity?
The cloud makes it easier and cost-effective for individuals and companies to access applications, store data, and communicate with other people. Other relevant technological forces, such as mobile, social, big data, AI and IoT are all built on the cloud. If you’re not moving towards a cloud strategy for your physical security, you’re closing yourself off from new technology. Why change platforms? Why do anything differently now? There’s one reason: better security at a better price. That’s what the cloud offers your business.
What’s at Stake?
If you wait too long to move to the cloud, you could end up being forced to make the change because your outdated technology is not supported or maintained any more. Making changes under conditions that are out of your control are never preferable. Your stakeholders expect solutions that are flexible, convenient and efficient. Modern security professionals should be able to provide data and know what is going on at all times at their facilities. Streaming surveillance video and integrated systems available through cloud solutions make this possible..
If you’re not migrating your physical security to the cloud, you’re limiting yourself. The efficiency and thoroughness required to function as a modern professional – especially in the physical security space – means that you need the right tools to get the job done.
When should you start looking at cloud solutions in physical security?
Start now. Cloud technology has been around for 20 years, it’s no longer new. The cloud is a safer option than onsite servers. Brivo, in particular, implements great safety measures to protect your physical security and data from cyber criminals. Think about these time frames when looking at migrating your physical security to the cloud:
- If you’re on a natural reset cycle, you have to replace equipment about every 2-4 years. The next time you’re at that juncture, slip the cloud migration into your normal refresh cycle.
- Take an incremental approach. Convert one product at a time as they become obsolete and you’re evaluating new solutions.
- For larger companies we see transitions happen when acquisitions take place. This time can be used as an opportunity to move to a new technology platform.
How to get executive support and sponsorship.
In a recent market research survey of 900 security professionals, 20.6% or respondents said their biggest pain point is getting executive buy-in on new technology.* Since it’s budget season, now is the time to get your c-suite onboard.
That same marketing research survey exposed that 21.6% of security professionals said their biggest pain point is cross departmental collaboration.
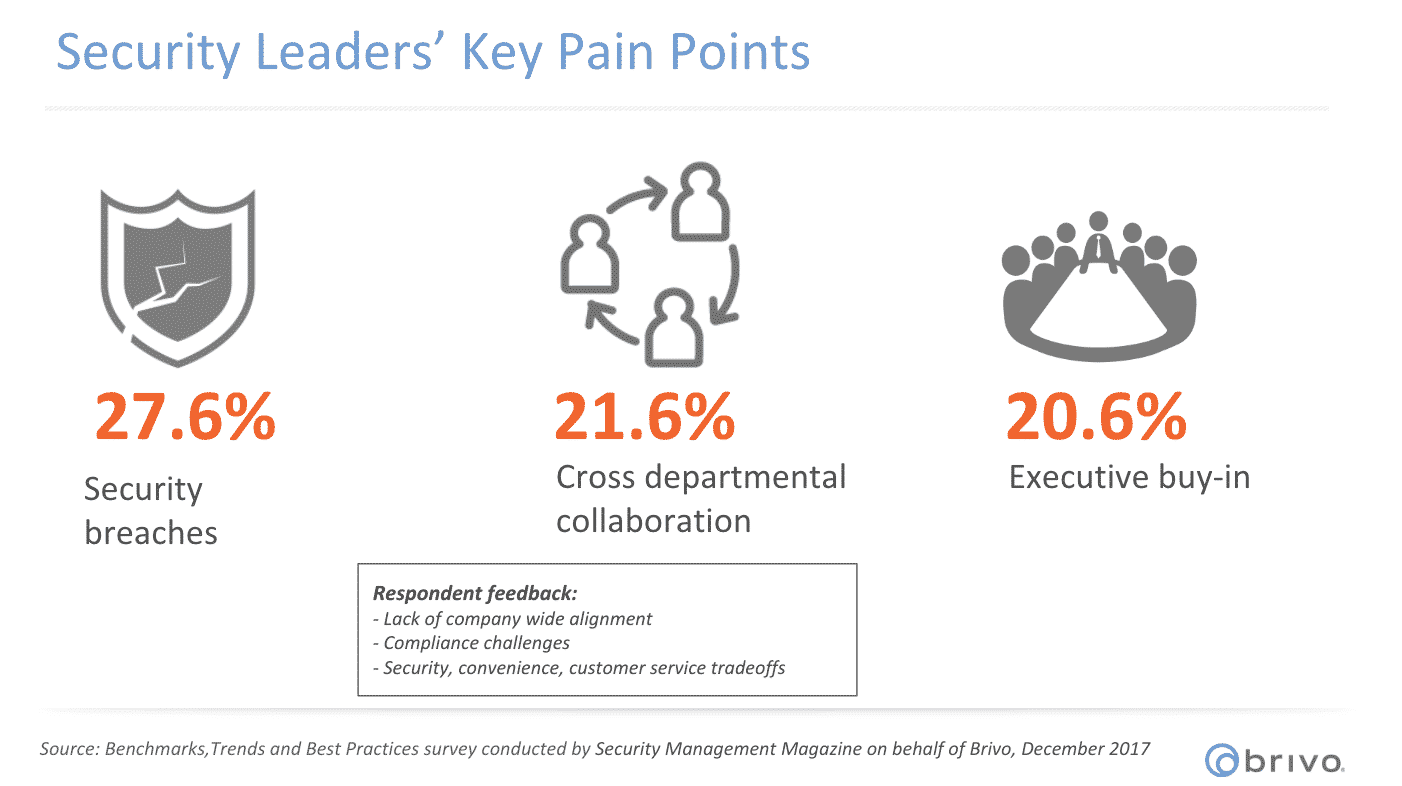 The good news is you can aleve both of these pain points at once. Getting executive buy-in and achieving cross departmental collaboration go hand-in-hand. Security leaders can gain IT buy-in by working closely with the IT department to validate the cybersecurity profile of the new cloud solution. The ease of launch, integration and low ongoing maintenance are benefits of cloud-based access control that the IT department appreciates.
The good news is you can aleve both of these pain points at once. Getting executive buy-in and achieving cross departmental collaboration go hand-in-hand. Security leaders can gain IT buy-in by working closely with the IT department to validate the cybersecurity profile of the new cloud solution. The ease of launch, integration and low ongoing maintenance are benefits of cloud-based access control that the IT department appreciates.
“Industry averages for electronic access control ranges $1000 to $5000 per door installed.” – IPVM . So, the best part about cross departmental collaboration is that it more commonly results in complete executive buy-in, and larger budget.
Executive buy-in happens when potential threats are understood and the proposed solution addresses those threats. Security and IT can lead the push to get all departments involved, including: HR, operations, and the executive team.
Here are some tools to help get executive and IT buy-in:
Selling to the C-Suite:
- Read tips to build a successful case to move to cloud-based access control
- See how to convince your leadership to upgrade to the cloud
ROI Resources:
- Learn how a national tech company improved operations by moving to the cloud
- See how another company is saving over a million dollars annually since they made the switch
Tools to Help with IT Buy-in:
- Read about the critical correlation between cybersecurity and physical security
- Get expert advice on how to be more physically secure by being more cyber secure
- Read about Brivo’s cyber secure technology
Is cloud-based access control safe?
Cloud-based access control is generally safer than on-premise solutions because security tests and software updates can be done automatically. Moreover, they are controlled by the cloud solution’s security experts who are devoted to cybersecurity. On-premise solutions require manual updates that can be missed or overlooked and leave systems vulnerable to hacks. As a provider of physical security services, we at Brivo believe that information security is of paramount importance to maintain the safety and security of your facilities. The methods Brivo uses to secure customer data are proven techniques based on industry best practices from existing Internet security technologies and the field of cryptography. You may want IT to help translate, but here are the basic ways Brivo ensures customer data remains protected:
- Authentication
- Digital Certificates and Public Key Infrastructure (PKI)
- Transport Layer Security (TLS)
Authentication
Authentication is the cornerstone of secure information exchange in Brivo Onair®, because each party must be able to verify that they are communicating with a trusted partner. Authentication is the process whereby each party verifies the mutual identity. Within the Brivo architecture, there are two exchanges requiring such verification: administrative login to the Brivo applications and control panel communication with the data center. Through this process, the administrator can be assured that access to an account in the Brivo system is legitimate.
Digital Certificates and Public Key Infrastructure
A digital certificate is an electronic document containing unique data that allows a device (or person) to authenticate itself to another device (or person). Its use in this context is part of a cryptographic protocol known as public key infrastructure or PKI. In the Brivo architecture, both the data center and the control panel have digital certificates that allow them to verify the identity of the other and subsequently encrypt their communications so it cannot be intercepted..
Transport Layer Security
TLS and its predecessor SSL are best known as encryption protocols favored by such secure web services as online banking, stock trading sites and ecommerce in general. It is used in these contexts because of its wide availability in commercial browsers and software libraries, and because it is highly secure. Properly implemented, TLS is virtually invulnerable to attack. In the Brivo Onair® architecture, both server and client certificates are used so that both parties can verify each other’s identity. Brivo implements every major information security precaution available to reliably meet our customers’ desire to be able to use the technology from anywhere, at any time. You can learn more about Brivo’s secure technology here .
How to find the right physical security solution for your company.
First, you need to define what you need in a physical security solution. Ask yourself some key questions:
- What are your security vulnerabilities?
- What do you need to protect?
- What features are you looking for?
- How does it need to function to fit the culture and needs of your business?
Your solution should address your physical security weaknesses, but the right solution has the power to improve business operations, save money and increase efficiency. Keep a few things in mind while you evaluate access control solutions:
- Pick a vendor you are comfortable with. Make sure you know how they keep your data secure and that they have a proven track record of consistent system uptime.
- Make sure your solution has the ability to integrate with other systems. System integrations are a necessity in most organizations. Your access control solution should be able to integrate with HR systems and building management systems for more effective and comprehensive security.
- The solution you choose should be flexible. It should be easy to know what is going on in your facility at all times. That means your solution should be mobile – full access to and control of your unified security platform from your mobile device.
- Your access control solution should be scalable. Choose a physical security solution that can easily change and grow with you.
Both scalability and flexibility are inherent in cloud solutions. Find out more about the right questions to ask your physical security vendor here.













