“Data insights don’t grow on trees any more than other scientific breakthroughs. They arise through very specific processes applied under the scientific method.” -Steve Van Till, President & CEO, Brivo
What good is a technological advancement in physical security if you can’t make better and more informed decisions?
The idea of big data and its potential impact on the physical security industry can be an overwhelming concept. Understanding what data types, basic access logs or video surveillance will be useful for your facility can be overwhelming. In step 3 of the toolkit, we covered IoT’s place in your technology roadmap. IoT-enabled devices produce the largest volume of big data information in the physical security industry, but tons of data alone isn’t enough. Big data should help us recognize threats earlier and make better choices.
To understand the impact of big data in physical security , it’s important to clearly define big data, develop a framework for the attributes that define big data, and understand the opportunity and requirements for big data to become smart data.
What Is Big Data?
Put simply, big data is the aggregation of information sets so large and complex that conventional data processing applications are inadequate. For our industry, big data means “situational intelligence.” This includes information like sensors data, employee key card credentials, area access logs, mobile or biometric identity verification, video surveillance and more. Multiply that by 365 days per year and you can see how each data set can really add up. As an organization grows, technological requirements change and this type of data storage should grow and adapt to your organization’s changing security needs.
What Characteristics Define Big Data?
These “ four V’s ” provide a framework for defining the attributes of big data:
- Volume
- Velocity
- Variety
- Veracity
Volume: Big data is big, but not based on a specific threshold. Volume refers to the data size requiring the development of new technologies for storage and processing.
Velocity: Velocity is the rate that data streams into an information system. Velocity also defined by how well it meets the required speed. This is typically where older, batch-oriented systems fail.
Variety: Variety describes the various structured and unstructured data types that are now part of modern analytics. For example time, tweets, video, voice and Bitcoin.
Veracity: The level of trust you have in the data. Some trust factors to consider are data accuracy, the method of collection, processing and the tools used.
However, big data is just big data until it’s actually refined and shaped into something useful. In physical security, the big goal is to be preventative and proactive through threat and abnormality recognition, not to aggregate logs of what happened after the fact.
The industry as a whole is not there yet, but there is a huge opportunity for big data to become smarter and more meaningful.
What’s the Opportunity?:
Collecting large amounts of security data is useful up to a point. It’s extremely helpful to have video and user access logs data when responding to a security event. However, the plateau for this big data is typically alert notification, event monitoring and reactive investigation. This still requires significant reliance on the human capability to navigate a sea of information and cull the important signals.
Defining and prioritizing what are significant signals depends on what the organization and security professional deem important. Obviously, you can’t anticipate all internal and external threats and even the best preventative measures have their limitations. Traditional on-premise access control systems face a major issue as security threats evolve: there is no simple way to learn from aggregate physical big data and evolve.
The way to overcome this challenge is to make big data smarter by adding machine learning (ML) and artificial intelligence (AI). In physical security, big data requires data sets across organizations in order to build better algorithms. That is best achieved through the cloud. Leveraging the power of AI. to analyze large data sets will potentially lead to faster recognition of abnormalities and proactive identification of threats. Unfortunately, machine learning embedded into physical security applications is not currently available as the industry as a whole is barely scratching the surface of this next frontier. However, it’s clear that this technology will be driven by cloud technology.
What’s at Stake?
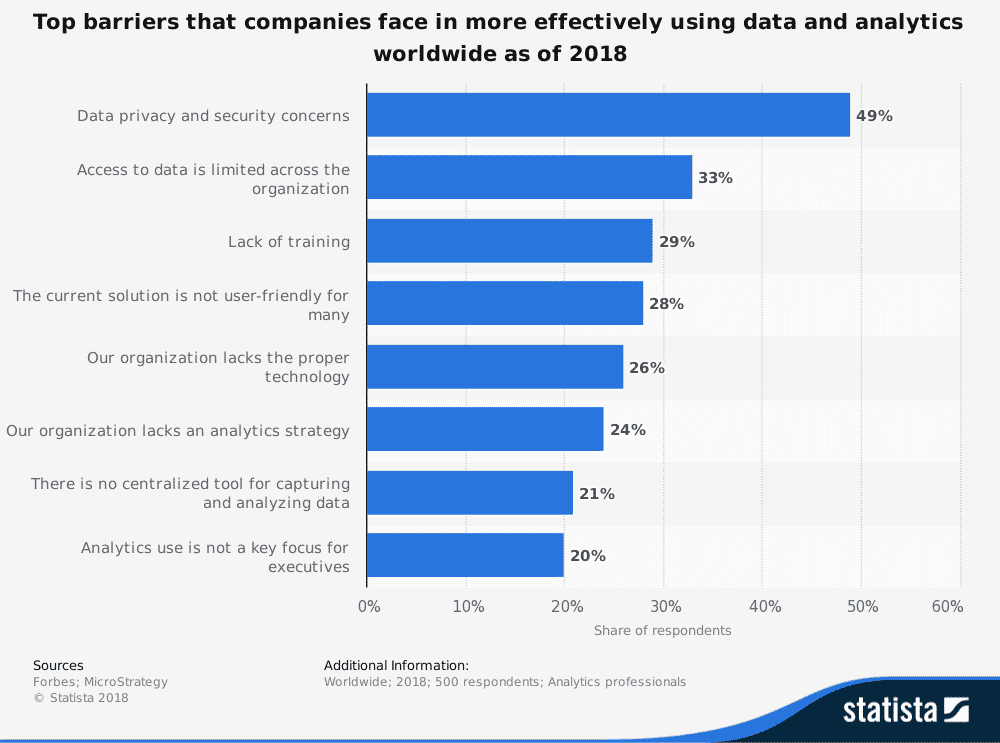
Adopting big data and analytics at the organizational level is also a challenge. In a recent survey, two of the biggest challenges a company faces regarding data use and analytics are:
- Limited access to data company-wide
- A lack of training on how to use data
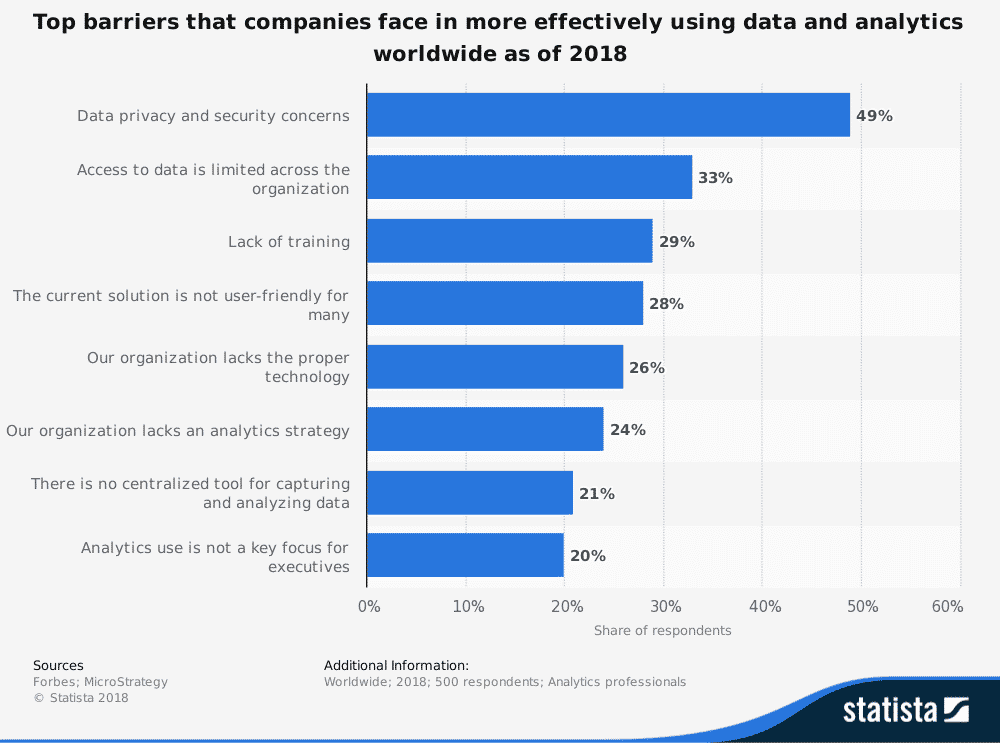 Limited access to and a lack of training for big data and analytics highlight a huge gap in the effectiveness of using big data. This may be okay for other industries, but in physical security, a lack of meaningful information or “situational intelligence” has more severe consequences.
Limited access to and a lack of training for big data and analytics highlight a huge gap in the effectiveness of using big data. This may be okay for other industries, but in physical security, a lack of meaningful information or “situational intelligence” has more severe consequences.
When Is It Time to Prepare for Smart Data?
In another recent survey, respondents stated that the biggest trend in big data is taking predictive models into production.
Unfortunately, production-ready smart data (AI + big data) embedded into physical security technology does not exist for our industry. One barrier to building effective machine learning algorithms is that a large number of organizations have yet to upgrade from traditional deployment, single-server access control systems to cloud solutions. Cloud allows for more integration potential than traditional systems and helps provide aggregated data across organizations. Aligning with the cloud now means building a foundation for the smart data of tomorrow. Listen to Brivo CEO Steve Van Till discuss the potential impact of smart data in physical security in the video below.
How Can I Build a Case to Prepare for Smart Data?
Security performance is gauged on how well we anticipate risk, respond to risk and the effectiveness of the response. Ultimately, organizations want to be better at threat detection. However, every organization has different needs and priorities. Determining the exact data needed to address those needs and priorities is key.
Organizational security technology should evolve as threats evolve. Cloud-based solutions are the future of the industry because they lay the foundation for smart data and better threat detection. Meeting each of the previous three steps of the Technology Roadmap for Building Security helps support the case for the smart data solutions of the future:
- Move to the Cloud (if you haven’t already)
- Adopt a Mobile Strategy
- Plan Your IoT Strategy
Following this roadmap aligns your building security plan with the benefits of cloud technology, move towards mobile credentials capabilities and integrate IoT into your physical security strategy. This provides critical big data that can transition into smart data when A.I. is introduced to the physical security industry.















